Our experience with Azure AD Application Proxy
Azure AD Applicaiton Proxy
Introduction
We recently received a request to demonstrate how internal web-based applications can be accessed from the Internet using Azure AD Application Proxy. This post details our journey and the outcomes of our testing.
What is Azure AD Application Proxy?
Azure AD Application Proxy is a feature of Azure Active Directory that allows remote access to applications. It functions as a reverse proxy, creating a bridge between users outside an organization's network and on-premises applications. This service offers a significant advantage over traditional solutions due to its seamless integration with Azure Active Directory, which allows for enhanced security measures like Conditional Access and Multi-Factor Authentication. Rather than exposing the internal network to the outside world, Azure AD Application Proxy allows applications to connect to the cloud, facilitating secure user access. This revolutionary feature supports web-based applications and even allows access to remote desktops and other network resources.
Setup Procedure
For our testing environment, we used Azure. We also set up an Azure AD environment to configure the enterprise application and Application Proxy Connector.
We followed the steps mentioned in the URL below to set up a Windows 2019 server and post the target application.
1. Created a Windows 2019 server in Azure.
2. Downloaded the App Proxy Connector from Azure AD Application proxy.
3. Installed the App Proxy Connector on the Windows 2019 server.
4. Waited for the connector to establish a connection to Azure AD.
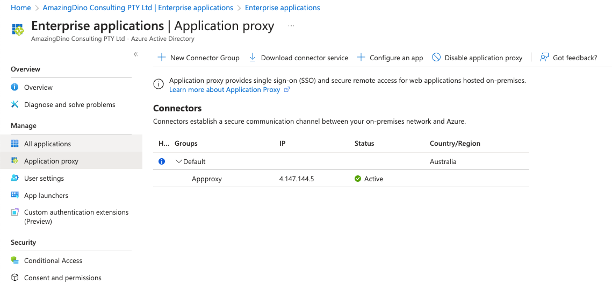
5. Setup Ubuntu VM with Nginx for application testing.
6. Setup Enterprise Applications and add the testing user in the Enterprise Applications.
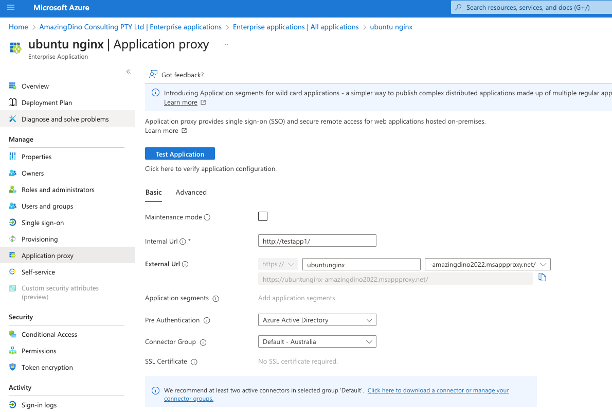
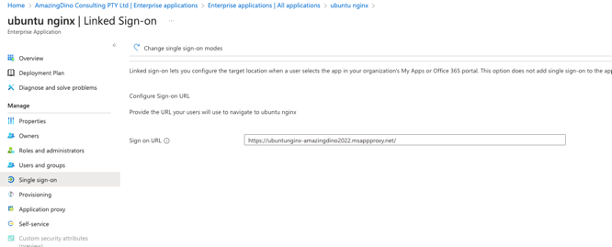
7. Configured "linked sign-on" to simplify the testing due to the absence of SSO integration.
Testing result
The testing user was able to navigate to
https://myapps.microsoft.com, authenticate using MFA, and access the testing app.

Caveats
Initially, we wanted to test this feature in the China 21Vianet region. However, we learned that Azure AD Application Proxy is currently not available in this region.
Conclusion
In summary, Azure AD Application Proxy proved to be a robust solution to our customer's requirement. It provided us with a secure method to enable remote access to a web-based intranet application while also facilitating MFA. Despite its limitations, such as non-availability in China, Azure AD Application Proxy shows promise for organizations striving to balance user access convenience with stringent security protocols. This experience underscores the importance of exploring and utilizing advanced features like Azure AD Application Proxy in similar scenarios. We welcome any discussions, queries, or sharing of personal experiences related to this topic.
References
- "What is Azure AD Application Proxy?" https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/what-is-application-proxy
- Azure AD Application Proxy setup procedure: https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-add-on-premises-application



